Malware masquerading itself as SEO plugin called WP-Base- SEO has infected reopen to 4 000 WordPress sites in the first two years according to security experts.
The intent of the programmers behind the malware is to hide in plain sight included as legitimate SEO plugin at the time creating backdoor to WordPress account...
That way should WordPress owner poke around and look for aware activities they easily adjoin it as SEO plugin. said Weston Henry lead security analyst security bank SiteLock that locate the real plugin.
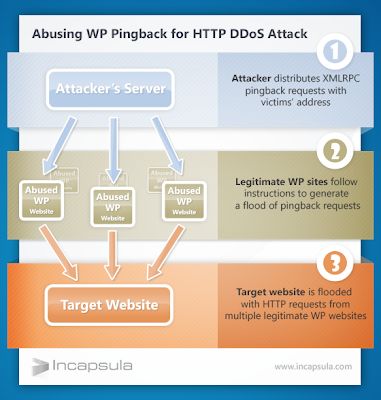
The means in which the plugin is being installed is possible via mass free imaging of WordPress sites where shark are looking for obsolete plugins or WordPress topic Henry said.
In July shark targeted WordPress page running RevSlider planting Neutrino Exploit Kit on webpages that attempted to install CryptXXX ransomware on visitors...
examination of the WP-Base- SEO malware reveals its malicious object in the type of base64 encoding PHP eval request according to blog that examines the plugin..
At glance the file seems to be legitimate like reference to WordPress plugin directory and documentation how the plugin works. according to the SiteLock..
This means that anytime the topic is loaded in server the reply is initialized. SiteLock said..
When researching first categories of WP-Base- SEO disease SiteLock said the plugin has need to buzz under the radar of many malware scanners..
In addition to imaging Henry said page executive need to be strange with issues associated with WordPress install and make sure they have number of plugins..
Read more
Related items: